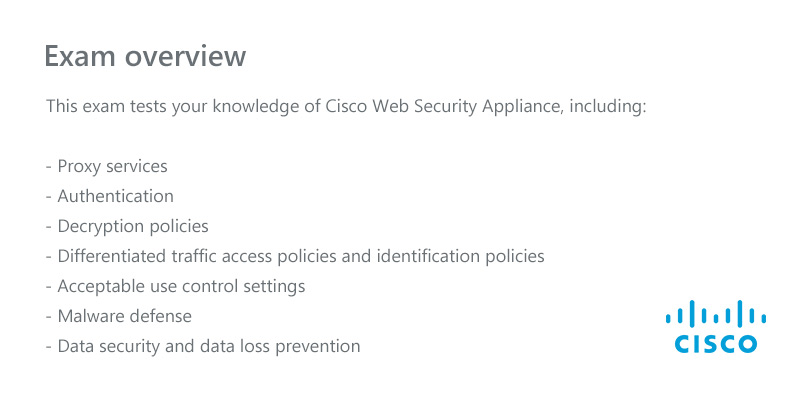
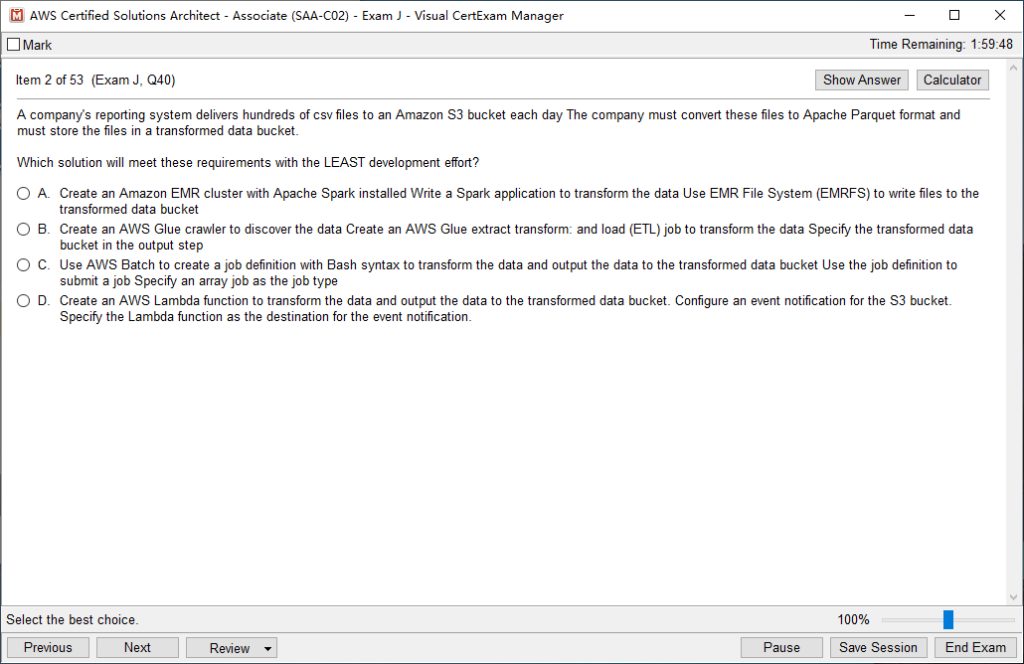
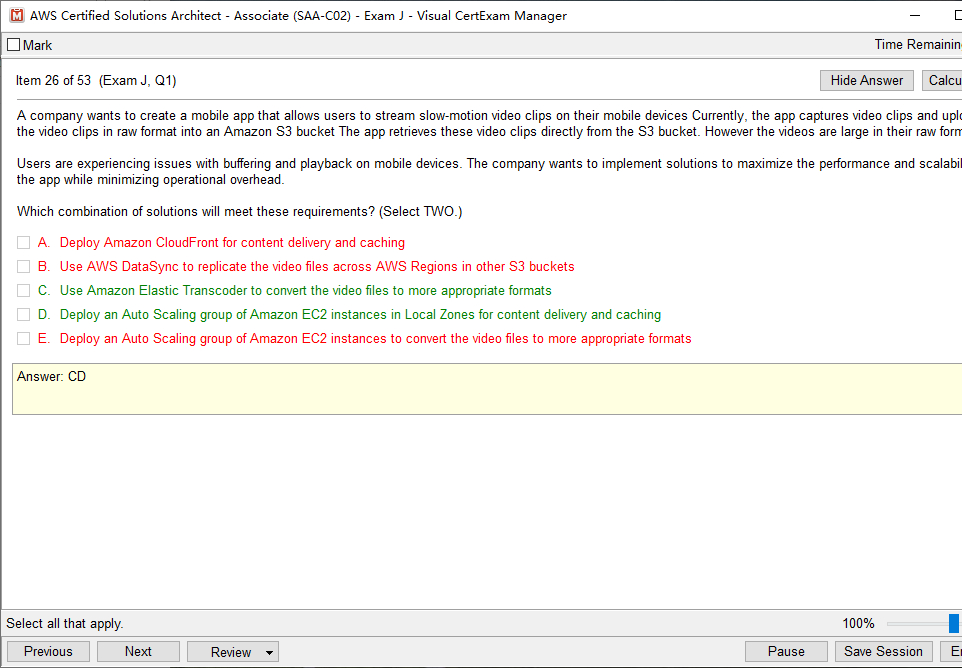
Leads4Pass CCNA 200-301 dumps are the latest update in 2025, including 1605 exam questions and answers. According to the actual requirements of CCNA certification, single & multiple choice, drag drop, simulation labs exam question types are formulated to help candidates feel the actual scenario exam.
View specific points:
Single & multiple choice1386Q&AsDrag drop181Q&AsSimulation labs38Q&AsUpdatedMar 19, 2025
CCNA 200-301 certification is a certification exam that most people have heard of. It is the entry-level exam for Cisco certification and mainly reflects the basic knowledge and practical ability of the network.
Welcome to use CCNA 200-301 dumps with PDF and VCE: https://www.leads4pass.com/200-301.html to help you pass the CCNA certification exam successfully. Next, I will continue to share some of the latest 2025 exam questions and answersfor free!
» Read more about: CCNA 200-301 dumps & Exam Practice Questions Shared 2025 »