
CyberOps Associate 200-201 dumps have been updated to the latest version, reviewed and corrected by the Cisco team, and conform to the actual certification exam!
CyberOps Associate certification (200-201 CBROPS Exam) is a prerequisite for entering the SOC security team! Passing the 200-201 CBROPS Exam is very important!
Therefore, leads4pass has updated the CyberOps Associate 200-201 dumps, which contain 264 latest exam questions and answers, which are real and effective exam materials!
Now, download CyberOps Associate 200-201 dumps with PDF and VCE: https://www.leads4pass.com/200-201.html to help you study easily and pass the exam successfully.
And share a free copy of CyberOps Associate 200-201 Dumps Exam Questions Online Practice
| From | Number of exam questions | Associated certification | Last update |
| leads4pass | 15 | CyberOps Associate | 200-201 dumps |
New Question 1:
What is the impact of false positive alerts on business compared to true positives?
A. True positives affect security as no alarm is raised when an attack has taken place, resulting in a potential breach.
B. True positive alerts are blocked by mistake as potential attacks affecting application availability.
C. False positives affect security as no alarm is raised when an attack has taken place, resulting in a potential breach.
D. False positive alerts are blocked by mistake as potential attacks affecting application availability.
Correct Answer: C
New Question 2:
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
A. swap files
B. temporary files
C. login sessions
D. dump files
E. free space
Correct Answer: CE
New Question 3:
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Correct Answer: B
New Question 4:
What is rule-based detection when compared to statistical detection?
A. proof of a user\’s identity
B. proof of a user\’s action
C. likelihood of user\’s action
D. falsification of a user\’s identity
Correct Answer: B
New Question 5:
An employee received an email from a colleague\’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender\’s address. What does this incident describe?
A. brute-force attack
B. insider attack
C. shoulder surfing
D. social engineering
Correct Answer: B
New Question 6:
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
A. CSIRT
B. PSIRT
C. public affairs
D. management
Correct Answer: D
New Question 7:
Refer to the exhibit.
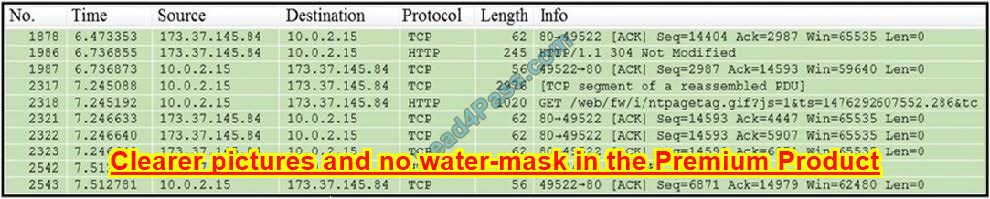
Which packet contains a file that is extractable within Wireshark?
A. 2317
B. 1986
C. 2318
D. 2542
Correct Answer: D
New Question 8:
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
A. server name, trusted subordinate CA, and private key
B. trusted subordinate CA, public key, and cipher suites
C. trusted CA name, cipher suites, and private key
D. server name, trusted CA, and public key
Correct Answer: D
New Question 9:
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by
sending the first SYN.
What is causing this issue?
A. incorrect TCP handshake
B. incorrect UDP handshake
C. incorrect OSI configuration
D. incorrect snaplen configuration
Correct Answer: A
New Question 10:
Refer to the exhibit.
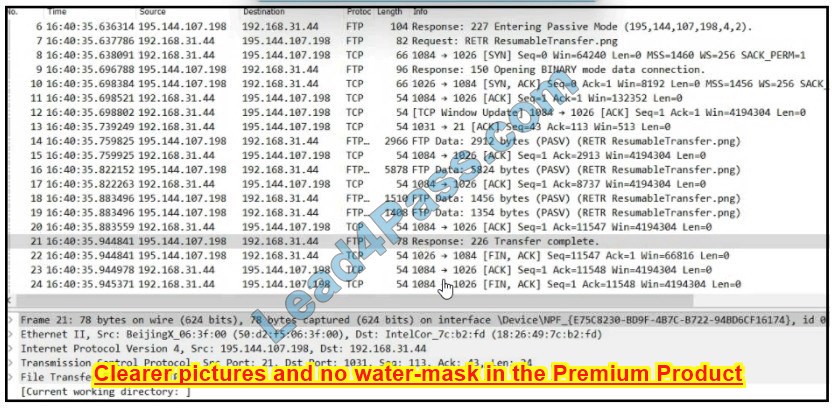
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
A. 7,14, and 21
B. 7 and 21
C. 14,16,18, and 19
D. 7 to 21
Correct Answer: B
New Question 11:
What is threat hunting?
A. Managing a vulnerability assessment report to mitigate potential threats.
B. Focusing on proactively detecting possible signs of intrusion and compromise.
C. Pursuing competitors and adversaries to infiltrate their system to acquire intelligence data.
D. Attempting to deliberately disrupt servers by altering their availability
Correct Answer: B
New Question 12:
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A. availability
B. confidentiality
C. scope
D. Integrity
Correct Answer: D
New Question 13:
Refer to the exhibit.
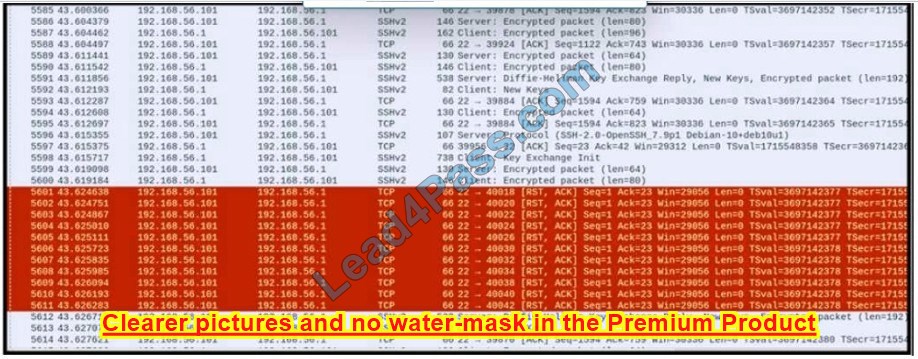
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
A. by using the buffer overflow in the URL catcher feature for SSH
B. by using an SSH Tectia Server vulnerability to enable host-based authentication
C. by using an SSH vulnerability to silently redirect connections to the local host
D. by using brute force on the SSH service to gain access
Correct Answer: C
New Question 14:
Refer to the exhibit.
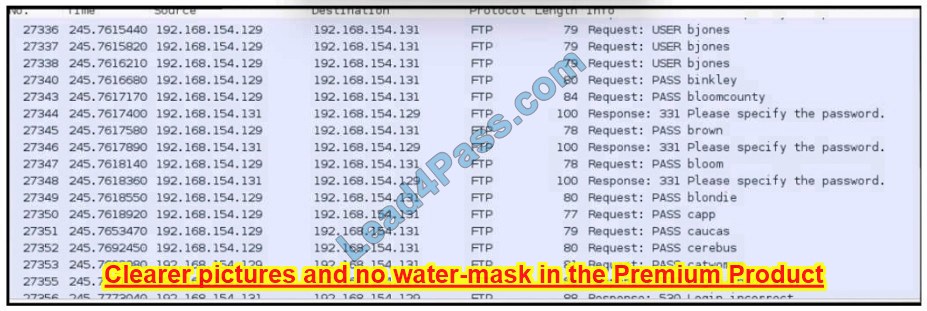
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
A. dstport == FTP
B. tcp.port==21
C. tcpport = FTP
D. dstport = 21
Correct Answer: B
New Question 15:
Which regex matches only on all lowercase letters?
A. [az]+
B. [^az]+
C. az+
D. a*z+
Correct Answer: A
…
The CyberOps Associate certification is the credential to enter the world of Cisco Cyber Security Operations! The condition is to successfully pass the 200-201 CBROPS Exam!
Participating in the online practice of CyberOps Associate 200-201 dumps exam questions can help you learn more practical and useful exam skills and improve your exam pass rate! The CyberOps Associate 200-201 dumps with PDF and VCE are now recommended:
https://www.leads4pass.com/200-201.html helps you pass the exam 100% successfully.