leads4pass 350-701 dumps updated to the latest version! 622 latest exam questions and answers fully updated by the professional team and verified to meet all requirements of 350-701 SCOR v1.1 exam topics!
Download the best material leads4pass 350-701 dumps for brand new topics: https://www.leads4pass.com/350-701.html, use PDF or VCE to help you practice easily and help you prepare for the new 350-701 SCOR exam prepare
Table of contents:
1. New 350-701 SCOR v1.1 Exam Topics
2. New 350-701 SCOR Exam Prep Information
3. Learn about the latest 350-701 exam questions
4. Summarize
Check out the latest 350-701 SCOR v1.1 exam topics online:

1.0 Security Concepts
- 1.1 Explain common threats against on-premises, hybrid, and cloud environments
- 1.1.a On-premises: viruses, trojans, DoS/DDoS attacks, phishing, rootkits, man-in-the-middle attacks, SQL injection, cross-site scripting, malware
- 1.1.b Cloud: data breaches, insecure APIs, DoS/DDoS, compromised credentials
- 1.2 Compare common security vulnerabilities such as software bugs, weak and/or hardcoded passwords, OWASP top ten, missing encryption ciphers, buffer overflow, path traversal, cross-site scripting/forgery
- 1.3 Describe functions of the cryptography components such as hashing, encryption, PKI, SSL, IPsec, NAT-T IPv4 for IPsec, preshared key, and certificate-based authorization
- 1.4 Compare site-to-site and remote access VPN deployment types and components such as virtual tunnel interfaces, standards-based IPsec, DMVPN, FlexVPN, and Cisco Secure Client including high availability considerations
- 1.5 Describe security intelligence authoring, sharing, and consumption
- 1.6 Describe the controls used to protect against phishing and social engineering attacks
- 1.7 Explain North Bound and South Bound APIs in the SDN architecture
- 1.8 Explain Cisco DNA Center APIs for network provisioning, optimization, monitoring, and troubleshooting
- 1.9 Interpret basic Python scripts used to call Cisco Security appliances APIs
2.0 Network Security
- 2.1 Compare network security solutions that provide intrusion prevention and firewall capabilities
- 2.2 Describe deployment models of network security solutions and architectures that provide intrusion prevention and firewall capabilities
- 2.3 Describe the components, capabilities, and benefits of NetFlow and Flexible NetFlow records
- 2.4 Configure and verify network infrastructure security methods
- 2.4.a Layer 2 methods (network segmentation using VLANs; Layer 2 and port security; DHCP snooping; Dynamic ARP inspection; storm control; PVLANs to segregate network traffic; and defenses against MAC, ARP, VLAN hopping, STP, and DHCP rogue attacks)
- 2.4.b Device hardening of network infrastructure security devices (control plane, data plane, and management plane)
- 2.5 Implement segmentation, access control policies, AVC, URL filtering, malware protection, and intrusion policies
- 2.6 Implement management options for network security solutions (single vs. multidevice manager, in-band vs. out-of-band, cloud vs. on-premises)
- 2.7 Configure AAA for device and network access such as TACACS+ and RADIUS
- 2.8 Configure secure network management of perimeter security and infrastructure devices such as SNMPv3, NetConf, RestConf, APIs, secure Syslog, and NTP with authentication
- 2.9 Configure and verify site-to-site and remote access VPN
- 2.9.a Site-to-site VPN using Cisco routers and IOS
- 2.9.b Remote access VPN using Cisco AnyConnect Secure Mobility client
- 2.9.c Debug commands to view IPsec tunnel establishment and troubleshooting
3.0 Securing the Cloud
- 3.1 Identify security solutions for cloud environments
- 3.1.a Public, private, hybrid, and community clouds
- 3.1.b Cloud service models: SaaS, PaaS, IaaS (NIST 800-145)
- 3.2 Compare security responsibility for the different cloud service models
- 3.2.a Patch management in the cloud
- 3.2.b Security assessment in the cloud
- 3.3 Describe the concept of DevSecOps (CI/CD pipeline, container orchestration, and secure software development)
- 3.4 Implement application and data security in cloud environments
- 3.5 Identify security capabilities, deployment models, and policy management to secure the cloud
- 3.6 Configure cloud logging and monitoring methodologies
- 3.7 Describe application and workload security concepts
View 350-701 SCOR v1.1 Exam Topics Complete
New 350-701 SCOR Exam Prep Information
The following share the new 350-701 SCOR Exam Prep Information after July 20, 2023, candidates can view the information to prepare, and provide a link to the complete content to help you view the original content.
| Exam Code | 350-701 |
| Exam name: | Implementing and Operating Cisco Security Core Technologies (SCOR) |
| Duration: | 120 minutes |
| Languages: | English and Japanese |
| Price: | $400 USD |
| Number of exam questions: | 90-110 |
| Passing Score: | 750-850 / 1000 Approx |
| Participation method: | In-person, Online (Provide online exam process) |
| coupon: | Cisco Learning Credits Exam Voucher Program |
The following video tutorial for Associate and Professional level exams will provide a walk-through demonstration of the various question types and how they function. View >>
Learn about the latest 350-701 dumps exam questions
| From | Type | Number of exam questions | Associated certifications |
| leads4pass | Free | 15/622 | CCNP Security |
Question 1:
A network administrator needs to find out what assets currently exist on the network. Third-party systems need to be able to feed host data into Cisco Firepower.
What must be configured to accomplish this?
A. a Network Discovery policy to receive data from the host
B. a Threat Intelligence policy to download the data from the host
C. a File Analysis policy to send file data to Cisco Firepower
D. a Network Analysis policy to receive NetFlow data from the host
Correct Answer: A
You can configure discovery rules to tailor the discovery of host and application data to your needs. The Firepower System can use data from NetFlow exporters to generate connection and discovery events and to add host and application data to the network map.
A network analysis policy governs how traffic is decoded and preprocessed so it can be further evaluated, especially for anomalous traffic that might signal an intrusion attempt -> Answer D is not correct.
Question 2:
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https:///capure/CAPI/pcap/test.pcap, an error 403: Forbidden is given instead of the PCAP file. Which action must the engineer take to resolve this issue?
A. Disable the proxy setting on the browser
B. Disable the HTTPS server and use HTTP instead
C. Use the Cisco FTD IP address as the proxy server setting on the browser
D. Enable the HTTPS server for the device platform policy
Correct Answer: D
Question 3:
What is offered by an EPP solution but not an EDR solution?
A. investigation
B. containment
C. sandboxing
D. detection
Correct Answer: C
Question 4:
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
A. With an on-premise solution, the provider is responsible for the installation and maintenance of the product, whereas, with a cloud-based solution, the customer is responsible for it
B. With a cloud-based solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product.
C. With an on-premise solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product.
D. With an on-premise solution, the customer is responsible for the installation and maintenance of the product, whereas, with a cloud-based solution, the provider is responsible for it.
Correct Answer: D
Question 5:
What is the benefit of flexible NetFlow records?
A. They are used for security
B. They are used for accounting
C. They monitor a packet from Layer 2 to Layer 5
D. They have customized traffic identification
Correct Answer: D
https://confluence.netvizura.com/display/NVUG/Traditional+vs.+Flexible+NetFlow
Question 6:
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
A. man-in-the-middle
B. cross-site scripting
C. insecure API
Correct Answer: A
Question 7:
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
A. It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
B. It discovers and controls cloud apps that are connected to a company\’s corporate environment.
C. It deletes any application that does not belong in the network.
D. It sends the application information to an administrator to act on.
Correct Answer: B
Question 8:
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
A. Configure the *.com address in the block list.
B. Configure the *.domain.com address in the block list
C. Configure the *.domain.com address in the block list
D. Configure the domain.com address in the block list
Correct Answer: C
Question 9:
An organization is trying to improve its Defense in Depth by blocking malicious destinations prior to a connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal?
A. Cisco Firepower
B. Cisco Umbrella
C. ISE
D. AMP
Correct Answer: B
ExplanationCisco Umbrella protects users from accessing malicious domains by proactively analyzing and blocking unsafe destinations. before a connection is ever made. Thus it can protect from phishing attacks by blocking suspicious domains when users click on the given links that an attacker sent.
Question 10:
Refer to the exhibit.
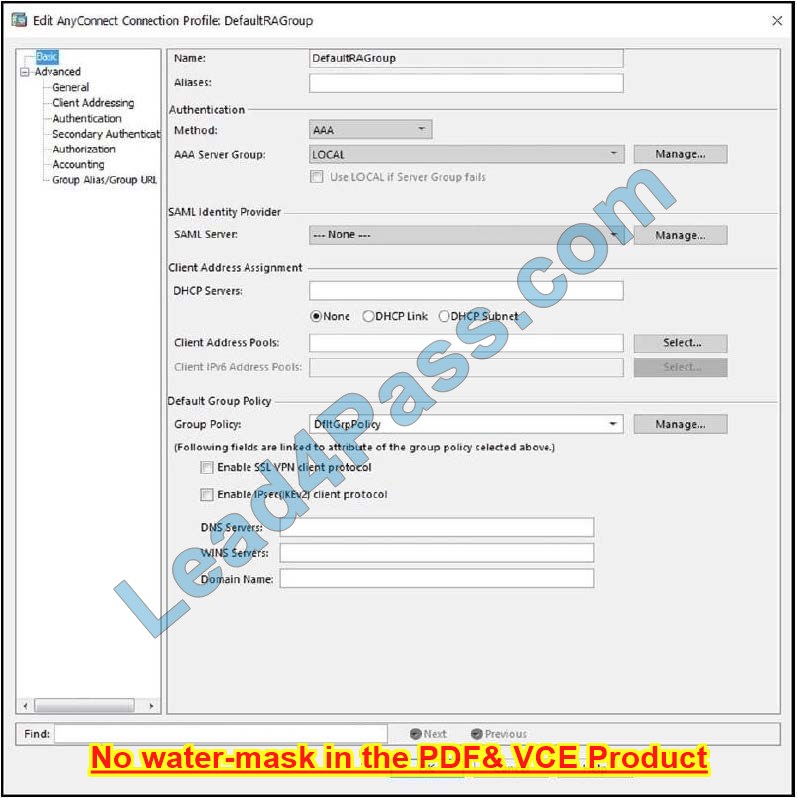
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates.
Which configuration item must be modified to allow this?
A. Group Policy
B. Method
C. SAML Server
D. DHCP Servers
Correct Answer: B
In order to use AAA along with an external token authentication mechanism, set the “Method” as “Both” in the Authentication.
Question 11:
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism.
Correct Answer: A
Question 12:
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
A. Application Control
B. Security Category Blocking
C. Content Category Blocking
D. File Analysis
Correct Answer: B
Question 13:
What is the benefit of installing Cisco AMP for Endpoints on a network?
A. It provides operating system patches on the endpoints for security.
B. It provides flow-based visibility for the endpoints network connections.
C. It enables behavioral analysis to be used for the endpoints.
D. It protects endpoint systems through application control and real-time scanning
Correct Answer: D
Question 14:
What is the function of Cisco AMP for Endpoints?
A. It detects DNS attacks
B. It protects against web-based attacks
C. It blocks email-based attacks
D. It automates threat responses of an infected host
Correct Answer: D
Question 15:
What is the benefit of using Cisco Umbrella?
A. DNS queries are resolved faster.
B. Attacks can be mitigated before the application connection occurs.
C. Files are scanned for viruses before they are allowed to run.
D. It prevents malicious inbound traffic.
Correct Answer: B
Summarize
The CCNP Security Core Exam “350-701 SCOR” has been updated and candidates will be tested on the new exam material beginning July 20, 2023!
To prepare for the new 350-701 SCOR exam leads4pass 350-701 dumps are also corresponding
A comprehensive update has been made to provide 622 newest exam questions and answers, which is the most effective exam material at present!
Candidates practice the exam material prepared for the 350-701 SCOR v1.1 exam topics in advance to guarantee 100% success on the exam.