
Why Use CyberOps Professional 350-201 Dumps?
CyberOps Professional 350-201 dumps come with two practice tools, PDF and VCE, to help users learn easily and complete the target work efficiently!
CyberOps Professional 350-201 dumps are updated throughout the year! And each update will participate in the actual scene verification to ensure that it is true and effective!
Use CyberOps Professional 350-201 dumps: https://www.leads4pass.com/350-201.html, get 139 latest exam questions and answers, and help you pass the exam 100% successfully.
Free use to some of the latest CyberOps Professional 350-201 dumps exam questions:
| From | Number of exam questions | Associated certifications | Last updated | Courses Online |
| leads4pass | 15 | CyberOps Professional | 350-201 dumps exam material | Udemy |
New Question 1:
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
A. Create a follow-up report based on the incident documentation.
B. Perform a vulnerability assessment to find existing vulnerabilities.
C. Eradicate malicious software from the infected machines.
D. Collect evidence and maintain a chain of custody during further analysis.
Correct Answer: D
New Question 2:
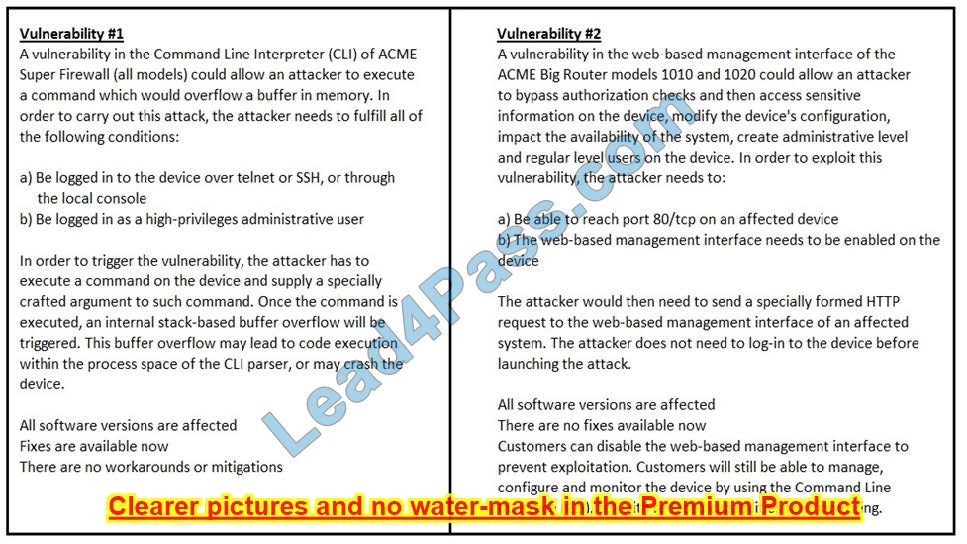
Refer to the exhibit. How must these advisories be prioritized for handling?
A. The highest priority for handling depends on the type of institution deploying the devices
B. Vulnerability #2 is the highest priority for every type of institution
C. Vulnerability #1 and vulnerability #2 have the same priority
D. Vulnerability #1 is the highest priority for every type of institution
Correct Answer: D
New Question 3:
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks. Which standard must the architect apply?
A. IEC62446
B. IEC62443
C. IEC62439-3
D. IEC62439-2
Correct Answer: B
New Question 4:
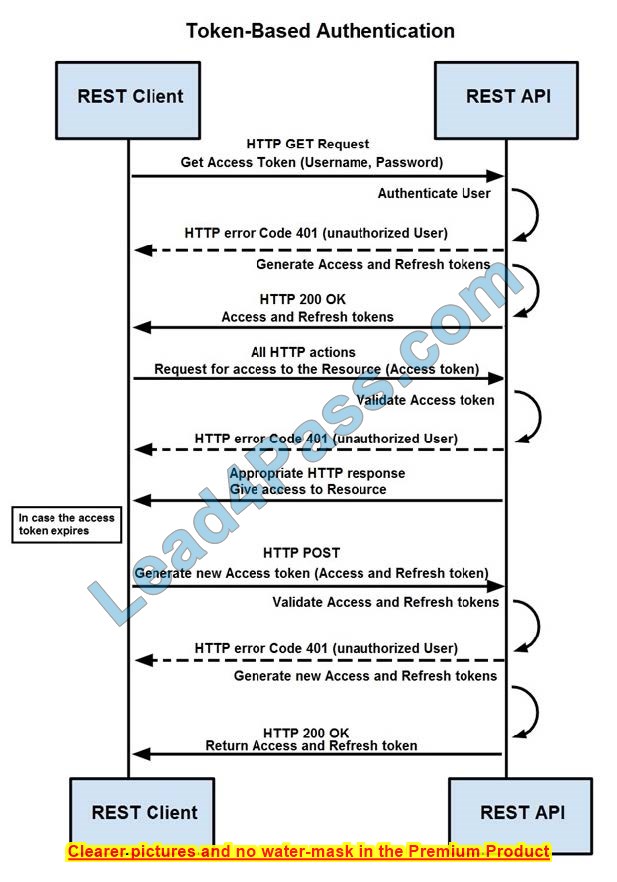
Refer to the exhibit. How are tokens authenticated when the REST API on a device is accessed from a REST API client?
A. The token is obtained by providing a password. The REST client requests access to a resource using the access token. The REST API validates the access token and gives access to the resource.
B. The token is obtained by providing a password. The REST API requests access to a resource using the access token validates the access token and gives access to the resource.
C. The token is obtained before providing a password. The REST API provides resource access, refreshes tokens, and returns them to the REST client. The REST client requests access to a resource using the access token.
D. The token is obtained before providing a password. The REST client provides access to a resource using the access token. The REST API encrypts the access token and gives access to the resource.
Correct Answer: D
New Question 5:
An engineer is analyzing a possible compromise that happened a week ago when the company? (Choose two.)
A. firewall
B. Wireshark
C. autopsy
D. SHA512
E. IPS
Correct Answer: AB
New Question 6:
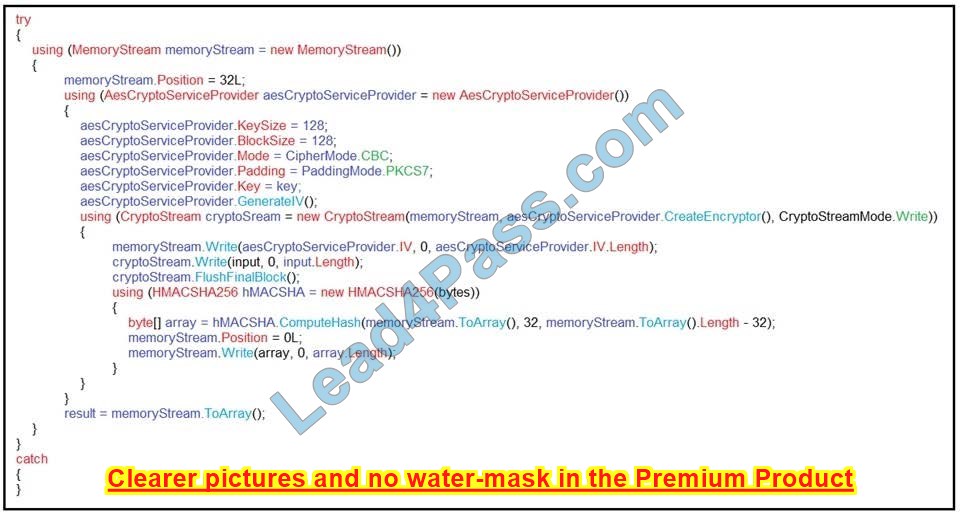
Refer to the exhibit. An engineer is performing a static analysis on malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?
A. The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard manufacturer, and connected removable storage.
B. The malware is ransomware querying installed anti-virus products and operating systems to encrypt and render unreadable until payment is made for file decryption.
C. The malware has moved to harvest cookies and stored account information from major browsers and configure a reverse proxy for intercepting network activity.
D. The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of loggers and webcam captures in locally encrypted files for retrieval.
Correct Answer: B
New Question 7:
A company recently started accepting credit card payments in their local warehouses and is undergoing a PCI audit. Based on business requirements, the company needs to store sensitive authentication data for 45 days. How must data be stored for compliance?
A. post-authorization by non-issuing entities if there is a documented business justification
B. by entities that issue the payment cards or that perform support issuing services
C. post-authorization by non-issuing entities if the data is encrypted and securely stored
D. by issuers and issuer processors if there is a legitimate reason
Correct Answer: C
New Question 8:
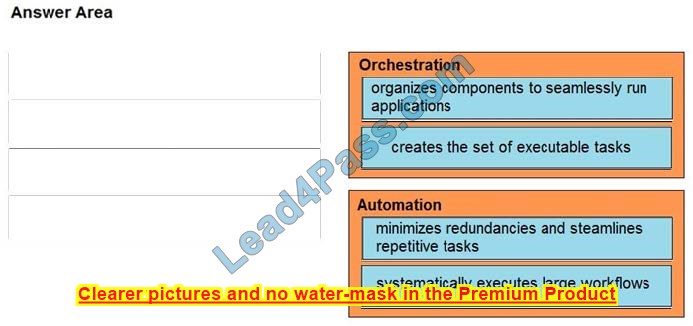
DRAG DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place:
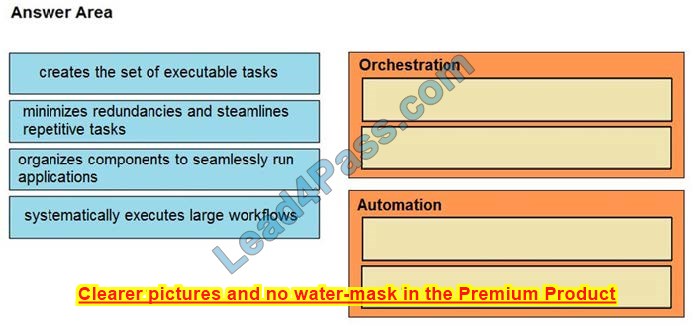
Correct Answer:
New Question 9:
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible. Which software development approach should be used to accomplish these goals?
A. continuous delivery
B. continuous integration
C. continuous deployment
D. continuous monitoring
Correct Answer: A
New Question 10:
An organization had several attacks over the last 6 months and has tasked an engineer with looking for patterns or trends that will help the organization anticipate future attacks and mitigate them. Which data analytic technique should the engineer use to accomplish this task?
A. diagnostic
B. qualitative
C. predictive
D. statistical
Correct Answer: C
New Question 11:
What is the limitation of cyber security risk insurance?
A. It does not cover the costs to restore stolen identities as a result of a cyber attack
B. It does not cover the costs to hire forensics experts to analyze the cyber attack
C. It does not cover the costs of damage done by third parties as a result of a cyber attack
D. It does not cover the costs to hire a public relations company to help deal with a cyber attack
Correct Answer: A
Reference: https://tplinsurance.com/products/cyber-risk-insurance/
New Question 12:
How is a SIEM tool used?
A. To collect security data from authentication failures and cyber-attacks and forward it for analysis
B. To search and compare security data against accepted standards and generate reports for analysis
C. To compare security alerts against configured scenarios and trigger system responses
D. To collect and analyze security data from network devices and servers and produce alerts
Correct Answer: D
Reference: https://www.varonis.com/blog/what-is-siem/
New Question 13:
Refer to the exhibit. Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy. Which method was used to signal ISE to quarantine the endpoints?
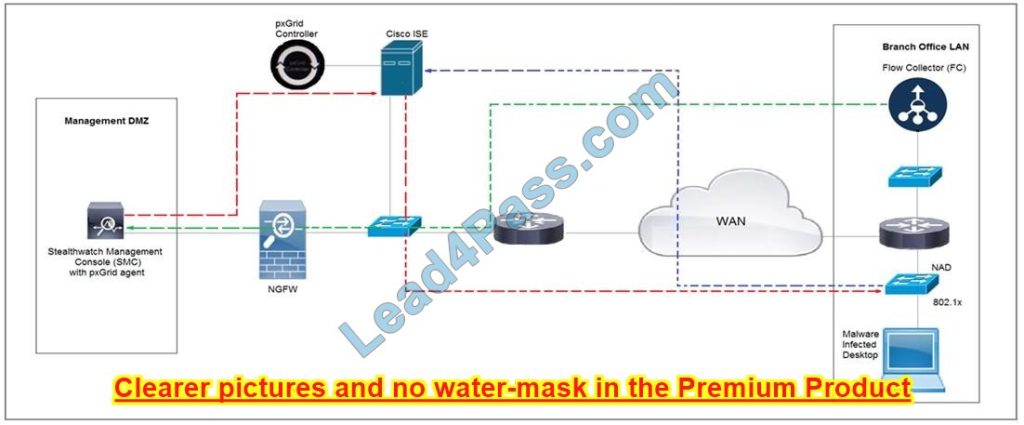
A. SNMP
B. Syslog
C. REST API
D. pxGrid
Correct Answer: C
New Question 14:
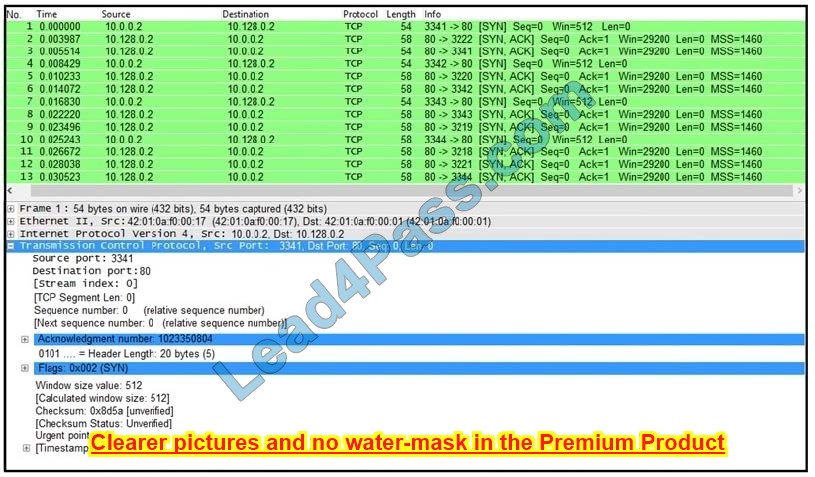
Refer to the exhibit. What is the threat in this Wireshark traffic capture?
A. A high rate of SYN packets being sent from multiple sources toward a single destination IP
B. A flood of ACK packets coming from a single source IP to multiple destination IPs
C. A high rate of SYN packets being sent from a single source IP toward multiple destination IPs
D. A flood of SYN packets coming from a single source IP to a single destination IP
Correct Answer: D
New Question 15:
A threat actor attacked an organization\’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers.
The threat actor successfully accessed the first server that contained sales data, but no files were downloaded.
A second server was also accessed that contained marketing information and 11 files were downloaded.
When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator\’s account was disabled.
Which activity triggered the behavior analytics tool?
A. accessing the Active Directory server
B. accessing the server with financial data
C. accessing multiple servers
D. downloading more than 10 files
Correct Answer: C
…
Why not use CyberOps Professional 350-201 dumps?
Candidates who have participated in the CyberOps Professional 350-201 certification exam know that when the 350-201 exam is updated with more new technical questions, the difficulty will increase accordingly! However, using CyberOps Professional 350-201 dumps
Candidates can have 365 days of free updates, which can help them cope with any technical upgrades! use CyberOps Professional 350-201 dumps: https://www.leads4pass.com/350-201.html Helping you cope with every upgrade!